ESG recently started offering TechTruths … single nuggets of data and the analyst perspectives of why they matter. Check out all of them via the link above, but here is my favorite so far on BYOD data protection:
So, why doesn’t IT back up BYOD endpoints?! It isn’t a rhetorical question.
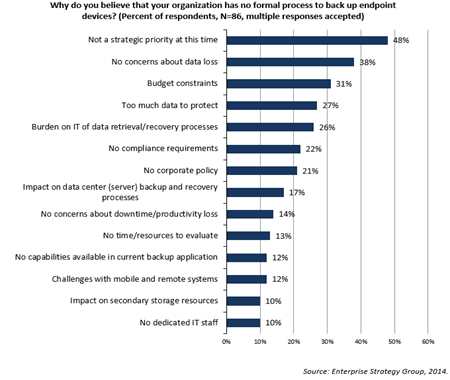
I have always been confounded why IT, the custodians of corporate data, doesn’t feel obliged to protect that corporate data when it resides on an endpoint device, and more particularly when the corporate data resides on a BYOD endpoint device. I understand the excuses – its hard to do well, the solutions are expensive, its difficult to quantify the business impact and therefore the ROI of the solution. In fact, in ESG’s Data Protection as a Service (DPaaS) trends report, we saw several excuses (not reasons) to not back up endpoint devices.
The myth that endpoint protection is hard and without justifiable value is old-IT FUD, in much the same way that tape is unreliable and slow. Both were true twenty years ago, and neither are true today.
Today, with the advent of all devices being Internet-connected, it’s never been easier to protect endpoint data, whether employer- or employee-owned. The real trick and one of the most interesting areas of data protection evolution is in the IT enablement of endpoint protection. It used to be that most viable endpoint protection solutions were consumer-only, meaning that IT was not only excluded from the process, they were unable to help when it matters. Today, real business-class endpoint protection should and does enable IT to be part of the solution, instead of the problem:
- Lightweight data protection agents that reach through the Internet to be protected, with user experiences that look like they came from an AppStore, instead of from the IT department.
- Encrypted connections in-flight and at-rest ensure the data is likely more secured while protected than it might be on the device itself.
- And most importantly, IT oversight – so that IT can do the same diligent protection of corporate data on endpoints that it does with corporate data on servers.
If you aren’t protecting your corporate data on endpoint devices, then you aren’t protecting your corporate data, period – and with today’s technologies, you are out of excuses (and reasons).
[Originally posted on ESG’s Technical Optimist.com]